Metaverse
Google uncovers malware campaign by China-linked hackers using Calendar events in a sophisticated cyberattack – Crypto News
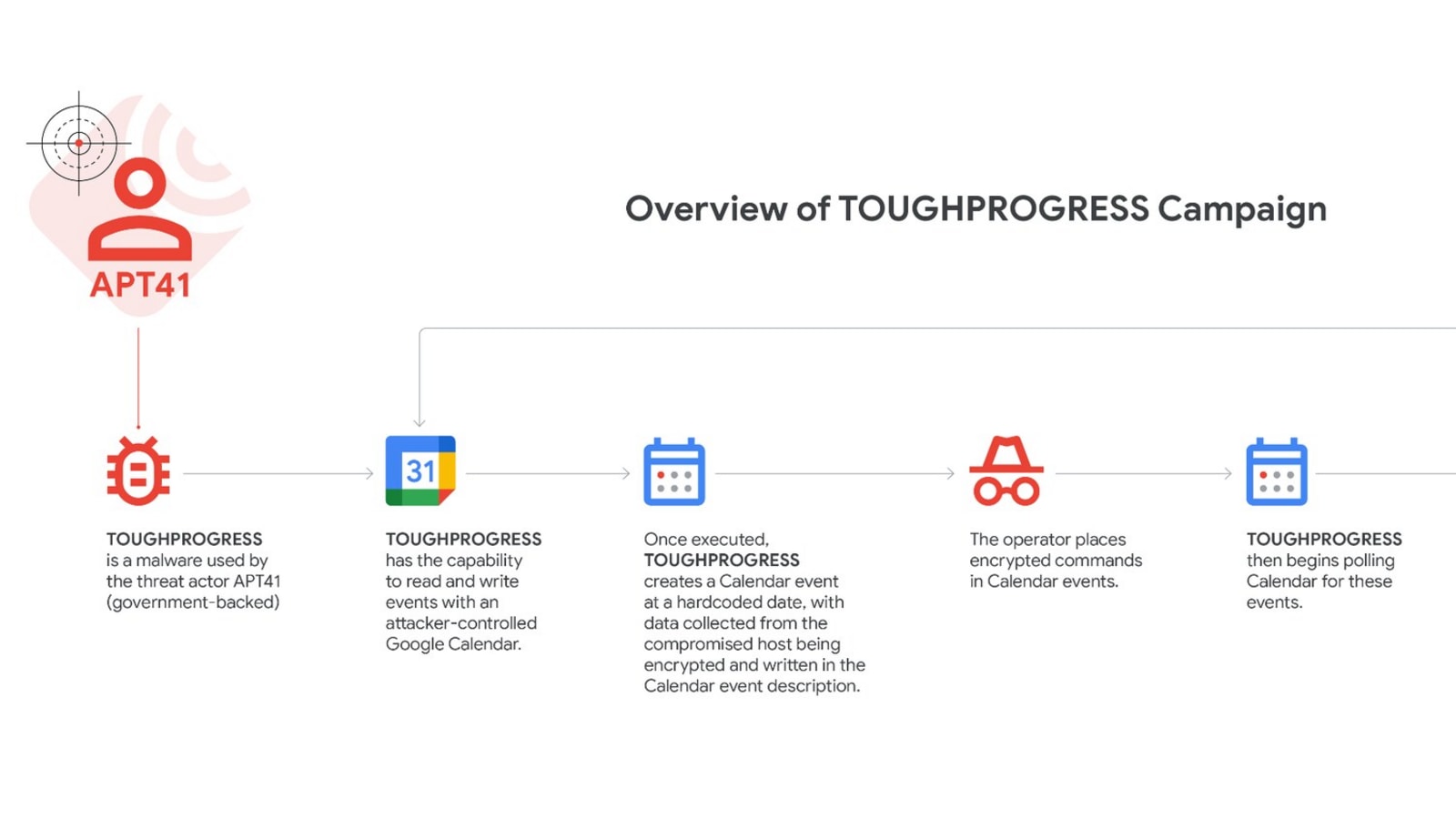
In a concerning revelation, Google’s Threat Intelligence Group (GTIG) has uncovered that a group of hackers linked to China used Google Calendar as a tool to steal sensitive information from individuals. The group, known as APT41 or HOODOO, is believed to have ties to the Chinese government.
According to GTIG, the attack began with a spear phishing campaign. This method involves sending carefully crafted emails to specific targets. These emails included a link to a ZIP file hosted on a compromised government website. Once the victim opened the ZIP file, they would find a shortcut file disguised as a PDF and a folder with several images of insects and spiders.
However, two of these image files were fake and actually contained malicious software. When the victim clicked the shortcut, it triggered the malware and even replaced itself with a fake PDF that appeared to be about species export regulations, likely to avoid suspicion.
The malware worked in three steps. First, it decrypted and ran a file named PLUSDROP in the computer’s memory. Then, it used a known Windows process to secretly run harmful code. In the final stage, a program called TOUGHPROGRESS carried out commands and stole data.
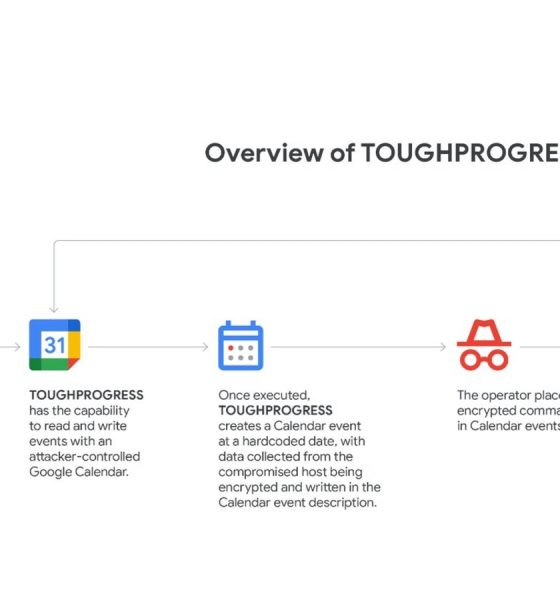
What made this attack unusual was the use of Google Calendar as a communication tool. The malware created short, zero-minute events on specific dates. These events included encrypted data or instructions hidden in their description field. The malware regularly checked these calendar events for new commands from the hacker. After completing a task, it would create another event with the stolen information.
Google said the campaign was discovered in October 2024 after it found malware spreading from a compromised government website. The tech company has since shut down the calendar accounts used by the hackers and removed other parts of their online infrastructure.
To stop similar attacks in the future, Google has improved its malware detection systems and blocked the harmful websites involved. It also alerted organisations that may have been affected and shared technical details to help them respond and protect themselves.
-

 Blockchain7 days ago
Blockchain7 days agoThe Quantum Clock Is Ticking on Blockchain Security – Crypto News
-

 Metaverse1 week ago
Metaverse1 week agoWould you raise an AI pet? India’s new digital companions are here – Crypto News
-

 Technology1 week ago
Technology1 week agoHow Americans are using AI at work, according to a new Gallup poll – Crypto News
-

 Technology1 week ago
Technology1 week agoHow Americans are using AI at work, according to a new Gallup poll – Crypto News
-

 Blockchain1 week ago
Blockchain1 week agoTether Launches Dollar-Backed Stablecoin USAT – Crypto News
-

 Metaverse3 days ago
Metaverse3 days agoContext engineering and the Future of AI-powered business – Crypto News
-

 Metaverse1 week ago
Metaverse1 week agoWould you raise an AI pet? India’s new digital companions are here – Crypto News
-
 Cryptocurrency1 week ago
Cryptocurrency1 week agoRiver Crypto Token Up 1,900% in the Last Month—What’s the Deal? – Crypto News
-

 Metaverse3 days ago
Metaverse3 days agoStop panicking about AI. Start preparing – Crypto News
-

 Metaverse1 week ago
Metaverse1 week agoWould you raise an AI pet? India’s new digital companions are here – Crypto News
-

 others1 week ago
others1 week agoUS Heiress Slaps Billion-Dollar Lawsuit on Banks for Allegedly Aiding the Looting of Her $350,000,000 Trust Fund – Crypto News
-

 Blockchain1 week ago
Blockchain1 week agoTrump-Backed WLFI Snaps Up 2,868 ETH, Sells $8M WBTC – Crypto News
-

 Blockchain1 week ago
Blockchain1 week agoTrump-Backed WLFI Snaps Up 2,868 ETH, Sells $8M WBTC – Crypto News
-

 Blockchain1 week ago
Blockchain1 week agoUS Storm Smashes Bitcoin Mining Power, Sending Hash Rates Tumbling – Crypto News
-

 Metaverse1 week ago
Metaverse1 week agoIs AI eating up jobs in UK? New report paints bleak picture – Crypto News
-

 Cryptocurrency1 week ago
Cryptocurrency1 week agoTrump family-backed American Bitcoin achieves 116% BTC yield – Crypto News
-

 Metaverse3 days ago
Metaverse3 days agoContext engineering and the Future of AI-powered business – Crypto News
-
Business1 week ago
New $2M Funding Reveals Ethereum Foundation’s New Threat – Crypto News
-

 Blockchain1 week ago
Blockchain1 week agoBitcoin Gets the Macro Bug as $87,000 Comes Into Play – Crypto News
-

 Cryptocurrency1 week ago
Cryptocurrency1 week agoMakinaFi hit by $4.1M Ethereum hack as MEV tactics suspected – Crypto News
-

 Technology1 week ago
Technology1 week agoHow Americans are using AI at work, according to a new Gallup poll – Crypto News
-

 others1 week ago
others1 week agoPBOC sets USD/CNY reference rate at 6.9843 vs. 6.9929 previous – Crypto News
-

 Cryptocurrency1 week ago
Cryptocurrency1 week agoRiver price defies market downturn, explodes 40% to new ATH – Crypto News
-

 Metaverse3 days ago
Metaverse3 days agoContext engineering and the Future of AI-powered business – Crypto News
-
others1 week ago
New $2M Funding Reveals Ethereum Foundation’s New Threat – Crypto News
-

 Cryptocurrency1 week ago
Cryptocurrency1 week agoAAVE drops 10% – Assessing if $1 trillion in loans can spark rebound – Crypto News
-
Technology1 week ago
Fed Rate Cut Odds in January Crash to 99% Ahead of Dollar Yen Intervention- Will BTC React? – Crypto News
-
Cryptocurrency1 week ago
Fed Rate Cut Odds in January Crash to 99% Ahead of Dollar Yen Intervention- Will BTC React? – Crypto News
-

 Blockchain1 week ago
Blockchain1 week agoBitcoin Gets the Macro Bug as $87,000 Comes Into Play – Crypto News
-
Business1 week ago
Bitcoin and XRP Price At Risk As US Govt. Shutdown Odds Reach 73% – Crypto News
-
Business1 week ago
Bitcoin and XRP Price At Risk As US Govt. Shutdown Odds Reach 73% – Crypto News
-
Business1 week ago
Bitcoin Sentiment Weakens BTC ETFs Lose $103M- Is A Crash Imminent? – Crypto News
-
Business1 week ago
Japan Set to Launch First Crypto ETFs as Early as 2028: Nikkei – Crypto News
-

 Cryptocurrency1 week ago
Cryptocurrency1 week agoRYO Digital Announces 2025 Year-End Milestones Across Its Ecosystem – Crypto News
-
 Cryptocurrency1 week ago
Cryptocurrency1 week agoRiver Crypto Token Up 1,900% in the Last Month—What’s the Deal? – Crypto News
-
Business1 week ago
Experts Advise Caution As Crypto Market Heads Into A Bearish Week Ahead – Crypto News
-
Business1 week ago
Experts Advise Caution As Crypto Market Heads Into A Bearish Week Ahead – Crypto News
-

 Blockchain1 week ago
Blockchain1 week ago‘Most Reliable’ Bitcoin Price Signal Hints at a 2026 Bull Run – Crypto News
-
Technology1 week ago
Bitcoin And XRP Price Prediction Ahead of FOMC Meeting Tomorrow, Jan 28 – Crypto News
-
Technology1 week ago
Bitcoin And XRP Price Prediction Ahead of FOMC Meeting Tomorrow, Jan 28 – Crypto News
-
Technology1 week ago
Bitcoin And XRP Price Prediction Ahead of FOMC Meeting Tomorrow, Jan 28 – Crypto News
-
Business1 week ago
Bitcoin Faces Renewed Volatility as Investors Explore Options Like Everlight – Crypto News
-

 Blockchain1 week ago
Blockchain1 week agoKalshi Expands Political Footprint with DC Office, Democratic Hire – Crypto News
-

 Technology1 week ago
Technology1 week agoElon Musk says ‘WhatsApp is not secure’ amid Meta privacy lawsuit; Sridhar Vembu cites ‘conflict of interest’ – Crypto News
-
Technology1 week ago
Fed Rate Cut Odds in January Crash to 99% Ahead of Dollar Yen Intervention- Will BTC React? – Crypto News
-
Business1 week ago
Bitcoin and XRP Price At Risk As US Govt. Shutdown Odds Reach 73% – Crypto News
-
others1 week ago
U.S. Shutdown Odds Hit 78% as CLARITY Act Faces Fresh Uncertainty – Crypto News
-

 others1 week ago
others1 week ago478,188 Americans Warned After Hackers Strike Government-Related Firm Handling Sensitive Personal Data – Crypto News
-

 Blockchain1 week ago
Blockchain1 week agoCZ Won’t Return to Binance, Bullish on Bitcoin Supercycle – Crypto News
-

 Blockchain1 week ago
Blockchain1 week agoSolana (SOL) Slips Further As Bears Target Deeper Support Zones – Crypto News