Technology
Malicious code found in fake coding extensions used to steal crypto – Crypto News
Security researchers have found open-source packages targeting developers with malware that steals cryptocurrency. The packages were hosted on the Open VSX repository disguised as tools for working with Solidity, a programming language used in blockchain development. They delivered malware that gave attackers control over victims’ devices and access to sensitive data.
The packages were meant to work with Cursor, a development environment based on Visual Studio Code. Cursor is often used for AI-assisted coding, making it a natural target for attackers looking to reach developers.
Kaspersky’s Global Research and Analysis Team uncovered the issue after a Russian blockchain developer reported an incident. The developer had installed what looked like a regular Solidity extension. Instead, it gave hackers access to his computer. They used that access to steal around $500,000 in cryptocurrency.
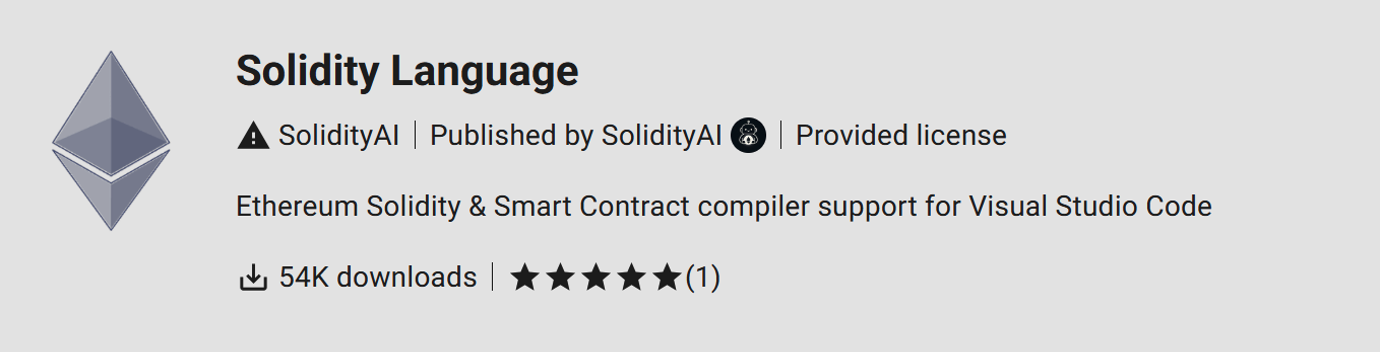
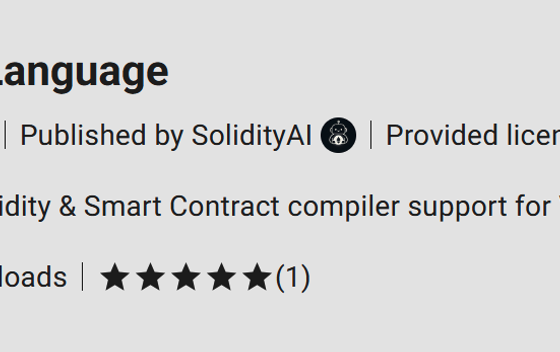
The attackers made their fake extension appear more trustworthy by pushing it higher in the repository’s search results by spoofing download numbers – pegging it at 54,000 installs. After being installed, the extension didn’t do anything useful. Instead, it installed ScreenConnect, a remote access tool that gave attackers full control of the machine.
From there, the attackers deployed Quasar, an open-source backdoor, along with a stealer tool. The combination collected data from the victim’s web browsers, email apps, and cryptocurrency wallets, including wallet seed phrases – critical information that allowed the attackers to drain accounts.
Once the original malicious extension was taken down, the attacker reuploaded it and faked more installs – this time claiming two million downloads (the real version of the extension had around 61,000 downloads by comparison). Kaspersky has flagged the fake version again for removal.
Georgy Kucherin, a researcher at Kaspersky, said these kinds of attacks are getting harder to spot. Even experienced developers who understand cybersecurity risks can fall for them, especially in fields like blockchain.
In addition to the fake Solidity extension, the attacker uploaded a malicious NPM package called solsafe, which also delivered ScreenConnect. A few months before that, three other harmful Visual Studio Code extensions – solaibot, among-eth, and blankebesxstnion – were uploaded to the same repository. Those have since been removed.
The attacks highlight how public code repositories are a growing threat vector, especially for developers working in sensitive fields like cryptocurrencies. Malicious packages disguised as helpful tools are proving to be a simple but effective way for attackers to gain access to high-value targets.
See also: Bitcoin’s rise puts cloud mining back on the table
-

 Metaverse1 week ago
Metaverse1 week agoWhat Satya Nadella’s latest shakeup says about Microsoft’s evolving AI strategy – Crypto News
-

 Metaverse1 week ago
Metaverse1 week agoWhat Satya Nadella’s latest shakeup says about Microsoft’s evolving AI strategy – Crypto News
-

 Technology1 week ago
Technology1 week agoAI isn’t the dot-com bubble, but that won’t stop it from ending badly – Crypto News
-
Technology1 week ago
Breaking: China Renaissance Bank Eyes $600M Raise for BNB-Focused Fund with YZI Labs – Crypto News
-

 Cryptocurrency6 days ago
Cryptocurrency6 days agoStripe’s stablecoin biz seeks national bank trust charter – Crypto News
-
Technology1 week ago
STON.fi CMO on Building TON’s Largest Swap & Liquidity Aggregator – Crypto News
-

 Technology1 week ago
Technology1 week agoBest phones under ₹15,000: Oppo K13 5G, Infinix Note 50s, iQOO Z10x and more – Crypto News
-

 others1 week ago
others1 week agoChina’s Commerce Ministry urges US to correct its wrong practices as soon as possible – Crypto News
-

 Technology1 week ago
Technology1 week agoChatGPT will soon pay for you! India’s AI payment pilot set to go live: What it means for users – Crypto News
-

 Blockchain1 week ago
Blockchain1 week agoCrypto Traders Show ‘Rationalization’ Behavior’ After Market Plunge – Crypto News
-

 Cryptocurrency1 week ago
Cryptocurrency1 week agoWhy Bitcoin could rebound up to 21% this week: experts explain – Crypto News
-

 Cryptocurrency1 week ago
Cryptocurrency1 week agoShiba Inu Burn Rate Crashes 99% as Crypto Sees Largest Liquidation Event Ever – Crypto News
-

 Metaverse1 week ago
Metaverse1 week agohuman intelligence for artificial minds – Crypto News
-

 others1 week ago
others1 week agoTrump’s tariff threat pushes US Dollar below 99 amid trade tensions – Crypto News
-

 others1 week ago
others1 week agoEUR/JPY retreats as Euro slides on French political uncertainty – Crypto News
-
others1 week ago
Binance Founder CZ Addresses BNB’s Recent Strong Price Performance, Says It Has No Market Makers – Crypto News
-

 others1 week ago
others1 week agoWhich way out of the range – Crypto News
-

 Metaverse6 days ago
Metaverse6 days agoWalmart teams with OpenAI for ChatGPT purchases. The retailer is ‘ahead of the curve’. – Crypto News
-
Technology1 week ago
Tom Lee’s Fundstrat Predicts Ethereum Rally to $5,500 Following ETH ‘Bottom’ – Crypto News
-
others1 week ago
Peter Brandt Flips Bullish on Bitcoin, Ethereum, XRP, and XLM – Crypto News
-

 Cryptocurrency1 week ago
Cryptocurrency1 week agoThe Latest Nobel Peace Prize Winner Is a Bitcoin Supporter – Crypto News
-

 others1 week ago
others1 week agoA balanced approach to monetary policy only works if inflation expectations are anchored – Crypto News
-

 De-fi1 week ago
De-fi1 week agoDeFi Withstands Stress Test as Market Mayhem Wipes Out Nearly $20B – Crypto News
-

 Metaverse1 week ago
Metaverse1 week agoIndia key to shaping future of Artificial Intelligence, says Anthropic CEO Dario Amodei after meeting PM Modi – Crypto News
-

 Cryptocurrency1 week ago
Cryptocurrency1 week agoCrypto liquidations drive historic market turbulence – Crypto News
-

 Blockchain1 week ago
Blockchain1 week agoHow to Use ChatGPT to Discover Hidden Crypto Gems – Crypto News
-

 Cryptocurrency1 week ago
Cryptocurrency1 week agoPolymarket bets trigger Nobel leak probe in Norway – Crypto News
-

 Cryptocurrency1 week ago
Cryptocurrency1 week agoHow Solana Overtook Ethereum’s Early Growth Curve – Crypto News
-
Technology1 week ago
Fed’s Anna Paulson Backs Rate Cuts, Downplays Trump Tariff Impact – Crypto News
-

 Cryptocurrency7 days ago
Cryptocurrency7 days agoPowell speech steadies crypto market: Fed hints at slower balance-sheet runoff – Crypto News
-
Business6 days ago
Pro Says Ethereum Price is a Buy Despite Rising Liquidations and BlackRock Selling – Crypto News
-
Business6 days ago
Pro Says Ethereum Price is a Buy Despite Rising Liquidations and BlackRock Selling – Crypto News
-

 Technology6 days ago
Technology6 days agoApple launches MacBook Pro 14-inch with M5 chip in India, price starts at ₹1,69,900 – Crypto News
-

 Cryptocurrency1 week ago
Cryptocurrency1 week agoDecoding WLFI’s meltdown – Can a $7mln buyback undo a $190mln dump? – Crypto News
-

 Cryptocurrency1 week ago
Cryptocurrency1 week agoHow Crypto Traders Are Positioning Following ‘Black-Friday’s’ Crash – Crypto News
-
others1 week ago
Crypto Market Braces for Volatility Ahead of Key U.S. Economic Events This Week – Crypto News
-
Technology7 days ago
XRP Price Crashes as Whales Dump 2.23B Tokens — Is $2 the Next Stop? – Crypto News
-

 Cryptocurrency7 days ago
Cryptocurrency7 days ago$23 Billion XRP Milestone Spotlighted by CME Group: Details – Crypto News
-

 others7 days ago
others7 days agoSeems ‘prudent’ to cut rates further given lower inflation risks – Crypto News
-

 Metaverse5 days ago
Metaverse5 days agoChatGPT ‘adult model’ plan: OpenAI’s Sam Altman reacts to criticism, says ‘not elected moral police’ – Crypto News
-

 Technology1 week ago
Technology1 week agoAmazon Diwali bonanza: Top 5 deals on flagship mobiles you should not miss – iPhone 16, OnePlus 13 & more – Crypto News
-
Business1 week ago
Is the Bitcoin Top In? Raoul Pal Signals Higher Liquidity Cycle Despite Market Selloff – Crypto News
-

 Technology1 week ago
Technology1 week agoGemini Nano Banana model now generates and edits images inside Google apps: How it works – Crypto News
-

 Technology1 week ago
Technology1 week agoHow to create 90’s retro-style Diwali AI portraits with Google Gemini Nano: 50 Viral prompts to try – Crypto News
-
Business1 week ago
Crypto Market Recovery: BTC, ETH, XRP, DOGE Surge 4-12% As Expert Sees V-Shape Upside – Crypto News
-

 Cryptocurrency1 week ago
Cryptocurrency1 week agoIs It Good to Invest in Ripple Now? – Crypto News
-
![Car Group Limited – CAR Elliott Wave technical analysis [Video]](https://dripp.zone/news/wp-content/uploads/2025/05/Car-Group-Limited-–-CAR-Elliott-Wave-technical-analysis-Video-400x240.jpg)
![Car Group Limited – CAR Elliott Wave technical analysis [Video]](https://dripp.zone/news/wp-content/uploads/2025/05/Car-Group-Limited-–-CAR-Elliott-Wave-technical-analysis-Video-80x80.jpg) others1 week ago
others1 week agoSamsara Inc. (IOT) laps the stock market: Here’s why – Crypto News
-
others7 days ago
Four Meme and BNB Partner on $45M ‘Rebirth Support’ Airdrop, First Batch Set to Begin – Crypto News
-

 Technology7 days ago
Technology7 days agoAMD strengthens AI push: Oracle to deploy 50,000 MI450 AI chips in data centers starting 2026 – Crypto News
-

 Cryptocurrency6 days ago
Cryptocurrency6 days agoBeyond Bitcoin: How Asia’s new crypto playbook is breaking from the west – Crypto News